It is no secret that the internet can be a dangerous place. With so much information – and misinformation – floating around, it is easy to get lost in the sea ...
Security
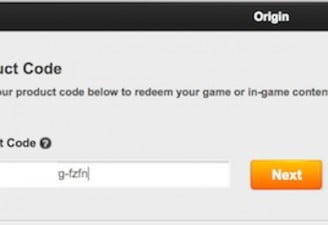
How to Retrieve Lost CD Keys and Codes Easily
Imagine that you’ve got a new PC rig and have to reinstall Windows and other important software. Usually, one costly realization sets in: You have lost the ...
How to delete Google location and activity history automatically
Google knows and remembers everything you do on your smartphone or web browser. It is scary how much Google knows about you. To restrict the search giant from ...
How to use old phones/tablets to increase home security
When you upgrade your phone or tablet, you may be wondering what to do with the old one. Some options include trying to sell it on the Internet, donating it, or ...
How to check if your account is affected after the massive Facebook data breach
A massive Facebook data breach ended up leaking phone numbers, Facebook IDs, birthdates, and users' emails on the internet for free. You must be thinking about ...
What is Cloud Security
The things cloud security comprises and the tools and equipment made to protect all the different cloud security aspects.Different aspects of cloud computing ...
How to use spy apps monitor a child’s social media activity
Children as young as ten now have their own smartphones, and growing up with smartphones being a normal part of their lives means that even younger children ...
How does a VPN protect user privacy and anonymity?
In the present day, privacy and anonymity are almost non-existent. This is because the internet has taken virtually all aspects of our lives online, and ISPs, ...
Solving common PC security threats with Outbyte AVarmor
Personal computers are used practically in all aspects of our lives. Be it working, studying, browsing the web, or playing games, all of this can be done if you ...
How to avoid email tracking in Gmail and Chrome
Believe it not; your email messages are probably being tracked. For anyone concerned about people watching us go about our daily lives, this fact is ...
The Role Of MSP In Improving The Internet Security Of A Business
The Role Of MSP In Improving The Internet Security Of A BusinessDamage linked to cybercrime is expected to hit a whopping $6 trillion annually by ...
Keeping your data more secure in 2023
Hackers have long been the bane of companies and individuals everywhere. I could write a book series about all the cybersecurity breaches that have taken place ...
Hackers are using an unpatched flaw to attack Windows 10 users
Microsoft announced that Windows 10 and other supported versions of Windows has a security flaw that can get a user infected with malware by just ...
Effortless ways to protect your smartphones from hacks
To say that this is the era of smartphones is an understatement. We’ve come to a point in our society that smartphones are the norm when it comes to ...
How to protect your email from hackers
Since we use email every day, we don’t often think of the dangers. It has become such an integral part of life that we almost take it for granted. But you ...